Configuring the Firewall for Windows Management Instrumentation (WMI) using Group Policy
You should not meet any difficulties when collecting the inventory data using WMI from domain computers. But unfortunately, problems occur sometimes. They can be caused by changing the security settings or by some other reason. If errors arise while the program is trying to access domain computers via WMI, the problem can be solved remotely with the help of the following instruction on using Group Policy settings.
Creating a group policy
Please note that the instruction is an example of a basic configuration of Group Policy.
-
Open the Domain Group Policy Editor Start - Run -
gpmc.msc (or use the keyboard shortcut Windows+R - gpmc.msc).
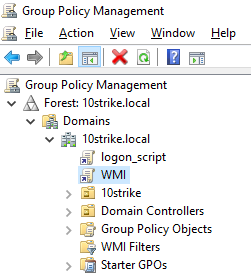
- Create a new group policy named WMI
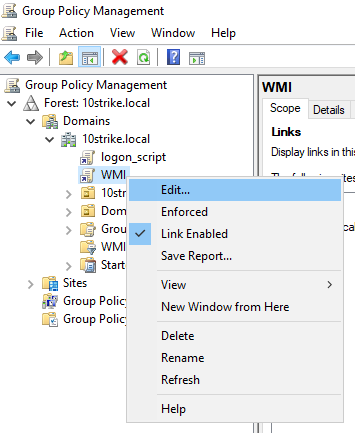
- Modify the WMI policy settings. Right click on it and click Edit.
- Navigate to Computer Configuration - Windows Settings - Security Settings - Windows Defender Firewall with Advanced Security - Windows Defender Firewall with Advanced Security
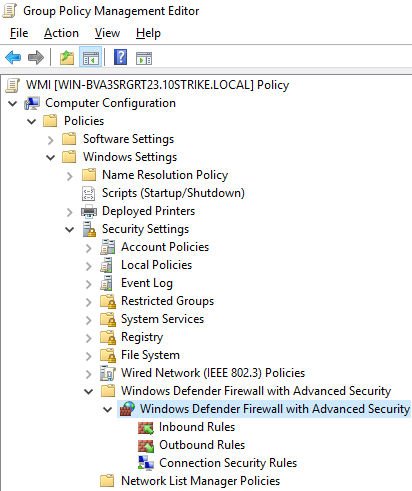
- Modify properties of the policy. Right click on the policy, then click Properties
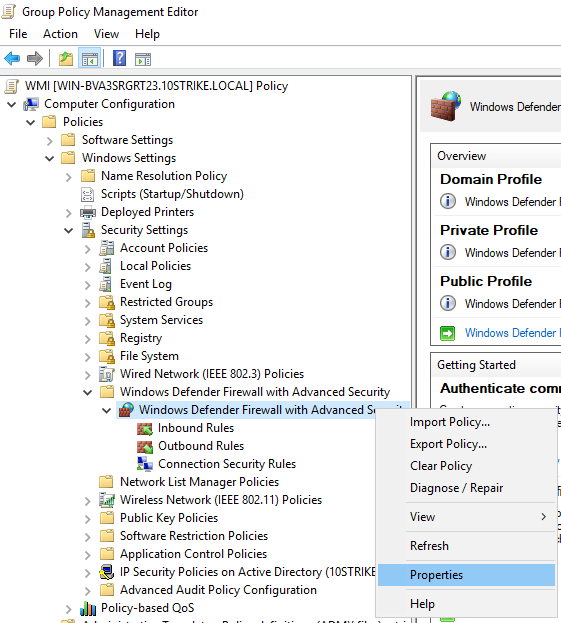
- Turn on the firewall for the domain (State = On)
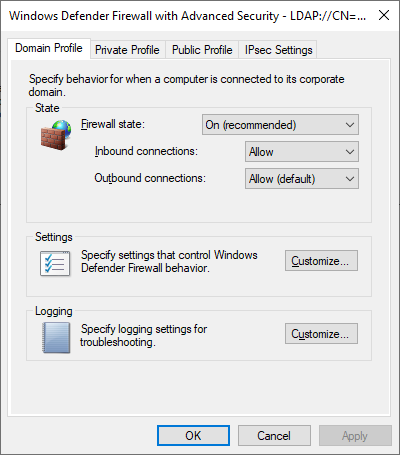
-
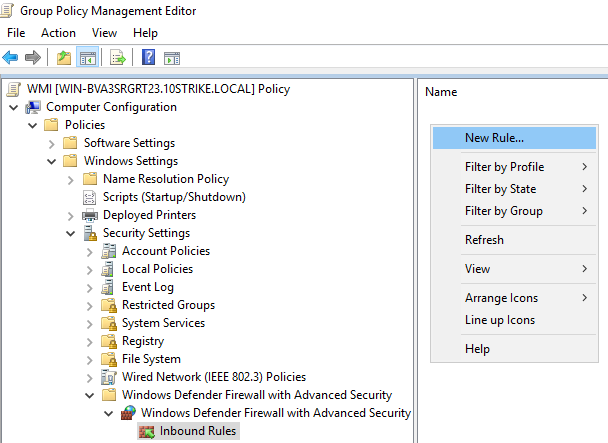
Create a new rule for incoming connections. Click Inbound Rules, then click by the right mouse button on the right panel's empty space, and click New Rule...
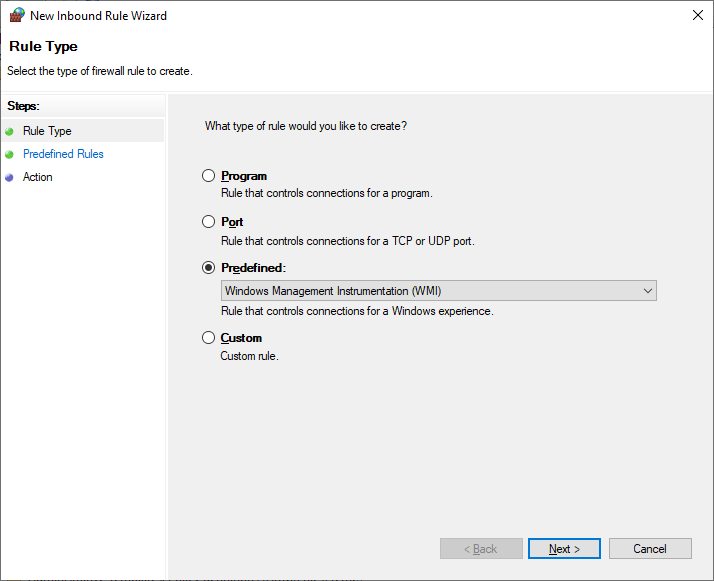
- In the "New Inbound Rule Wizard" window that opens, select "Predefined" and select the "Windows Management Instrumentation (WMI)" item in the drop-down list.
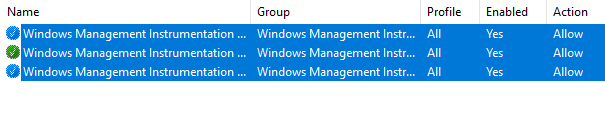
- If all the steps were performed correctly, there will be three enabled and allowed policies (green) on the right panel.
See also:
WMI Access Troubleshooting Guide
WMI Polling Errors Displayed by the Program
Frequently Asked Questions (FAQ)