![]() Starting the network scanning wizard
Starting the network scanning wizard
![]() Step 1. Specifying IP address ranges
Step 1. Specifying IP address ranges
![]() Step 2. Specifying a scanning method and configuring options
Step 2. Specifying a scanning method and configuring options
![]() Step 3. Finding and selecting computers for placing on the monitoring list
Step 3. Finding and selecting computers for placing on the monitoring list
You can create the list of network hosts with the Network Scanning Wizard. Creating a host list takes several steps:
![]() 1. Starting the Network Scanning Wizard.
1. Starting the Network Scanning Wizard.
For that purpose, click on the File item on the main menu and then select Scan Network.
![]() 2. Selecting a scanning method.
2. Selecting a scanning method.
The Wizard uses two methods for searching network devices:
- Scanning IP range
This method allows you to spot the maximum number of devices. It features the following advantages:- High scanning speed
- Recognition of diverse hardware types: printers (local and network), switches, hubs, servers, database servers, routers, WiFi access points, etc.
- Combination of several efficient network hardware search methods (ICMP ping, scanning a series of TCP ports, ARP requests)
- Retrieving data from hardware via SNMP (switches, printers, WiFi, etc.)
- You can scan several IP ranges at once
- Importing from the Network Neighborhood
This method works somewhat faster than the other one; however, not all devices are guaranteed to be found (computers only).
Importing from Network Neighborhood does not involve difficulties. What we are to learn in detail is scanning IP range.
![]() 3. Step 1. Specifying IP address ranges.
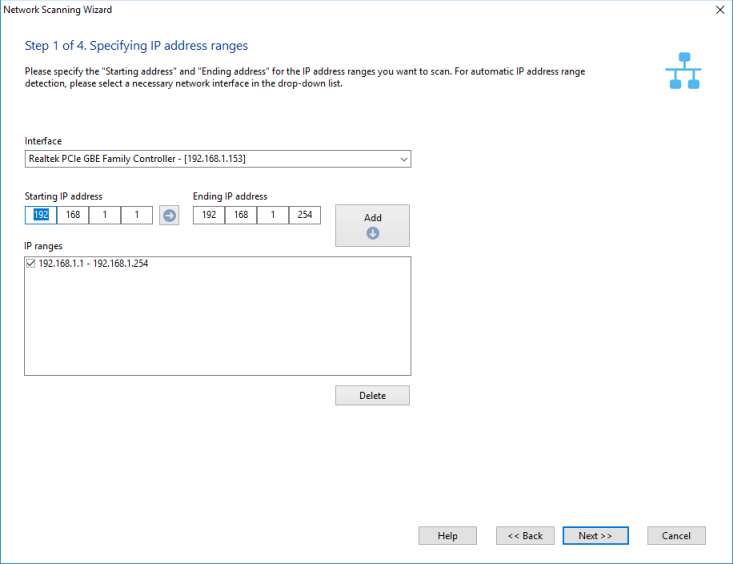
3. Step 1. Specifying IP address ranges.
On the first step we configure IP ranges to be scanned:
1) In the fields Starting IP address and Ending IP address enter the range of IP addresses to be scanned. To automatically detect the range of IP addresses applicable to your network, select the current network interface card (the Interface drop-down box).
2) Once the address fields are filled in, click on the Add -> button, and the selected range will be added to the list of IP ranges to be scanned. To Delete a range from the list, simply click on the corresponding button. Tick off the IP ranges on the list that are to be scanned.
3) Click the Next>> button.
![]() 4. Step 2. Specifying a scanning method and configuring options.
4. Step 2. Specifying a scanning method and configuring options.
The wizard allows you to choose from three different methods for searching for devices on a network:
- ICMP ping
The Packets parameter defines the number of ICMP packets to be sent by the application to each address to be scanned. In heavy-load networks, sending just one packet may be insufficient to receive a response from an existing host. In this case, it's recommended that you set at least 3-4 packets.
- Scanning TCP ports
Scanning TCP ports requires a list of Ports, by which devices could be found on a network. The most widespread open ports in Microsoft networks are 139 (NetBIOS), 21 (FTP), and 80 (HTTP).
IMPORTANT! When selecting a port scanning method, please keep in mind that in the majority of cases firewalls may consider your actions an attack if you scan several ports on a host at a time, and that may cause the respective consequences.
Windows XP and newer operating systems do not allow scanning groups of TCP ports simultaneously and intentionally slow down the process on the driver level.
- ARP ping (IP->MAC)
ARP requests are attempts to resolve a host's MAC address by its IP address. If the MAC address can be resolved, the Wizard will add the host to the list of search results. There is a chance that the program can find non-existing hosts. The address table in a switch can keep the old or reserved data. In such cases, clear the checkboxes next to the items in the results window.
For all scanning methods you must set the Response timeout, which defines how long the wizard will wait for a response from the host being scanned.
The perfect choice of search parameters depends on your network configuration, availability and functioning of the necessary protocols. In particular, to detect hosts in a local area network with bandwidth of 100 Mbps and higher, Two ping packets and a 100-500 ms response will be sufficient. In the case with TCP ports , it is worth noting that the greater number of ports you specify on the list, the longer the application will search for hosts in the network. The best way to go around this is to set the 2-3 most common ports through which the application can find Windows stations and servers; those include 139, 21 and 80th (NetBIOS, FTP, HTTP).
Searching for network printers is a different story. This procedure takes quite a bit of time, and therefore it should not be run if you are sure that there are no such printers in your network. Otherwise, you would have to wait for the completion of that procedure. The completion will be indicated by the appearance of the network scanning progress bar in the network scanning wizard window. The reason why the procedure is so slow is because it searches for network printers before launching the primary scanning procedure (which is performed with a large number of threads running simultaneously, unlike with searching for printers).
The wizard can automatically find all servers, database servers in your network, obtain other useful information on found computers (OS type, comment, etc.) To enable retrieving that additional information, select the option Get additional data on hosts via NetBIOS . This function will work only if the NetBIOS protocol is allowed on your computer and in other computers in your network. If the NetBIOS protocol is disabled in your network, no such information can be retrieved, and the application will spend quite a bit of time on that attempt (hence the feeling that the application is “frozen”). Searching for network switches is done in the multithreaded mode. However, if you specify a large number of possible community string values, that will also slow down the scanning process. Hence, if you have set the scanning parameters, and the application is scanning too slow or, even worse, completely "frozen" – go ahead and disable some of those parameters (first, disable network printer search and then disable obtaining additional information through NetBIOS) and try launching the scanning procedure again.
To discover IP cameras on the network, use the Search CCTV cameras by RTSP option (cameras must have RTSP enabled).
Default Checks
When the found hosts are added to the monitoring list, the program can automatically assign them the ping and/or the performance checks. You can configure the default checks in the program settings. The performance monitoring requires access to WMI on remote computers. Specify usernames and passwords for this, and enable the WMI availability check.
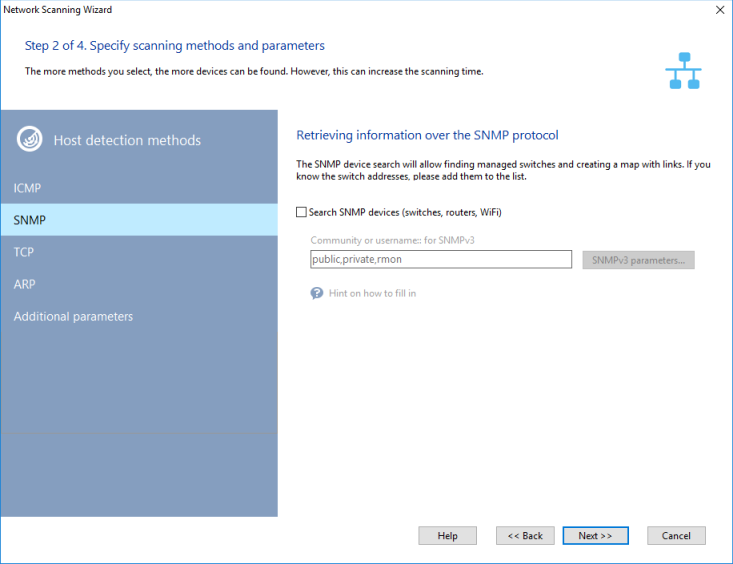
SNMP Search
If you have devices with an active SNMP agent in your network, the wizard will display the description for those devices. Such active SNMP agents help the wizard to detect a more diverse range of hardware types. Thus, for example, from the information obtained via SNMP, the wizard can identify switches, hubs, routers, printers, WiFi access points, wireless routers, etc. When searching for hardware with an active SNMP agent, the wizard attempts to connect to the next address using the defined community names (Community). Those names can be listed in the Community strings field, separated with commas. The most commonly used community names set by default are public, private, rmon . If you know that your hardware uses other names, please add them to the list.
The program supports the SNMPv3 protocol - a secure version of SNMP. Specify a username and password (through the # symbol: username#password) instead of the Community string in this case.
You can scan Virtual LANs and read the MAC address tables from VLANs configured on managed Cisco switches if you use them. To do this, please specify all VLAN numbers with your community strings using the @ sign in the Community strings field. For example, public@1, public@2, public@100 (this will poll VLANs 1, 2, and 100). The program will poll all the listed VLANs and get MAC addresses from them to find devices and draw links. This function works on Cisco switches only!
Building Network Map
This functions works the Pro version only.
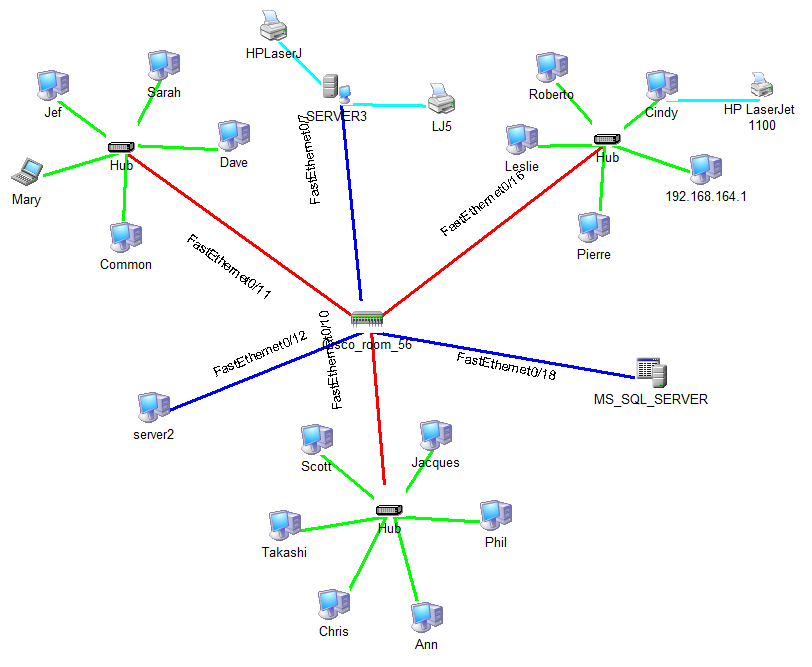
During the scanning process, the program discovers the network topology, connects to managed switches via the SNMP protocol, and obtains the information about connections between hosts. The program draws a network diagram, connecting the icons of the found devices with lines.
Link Information
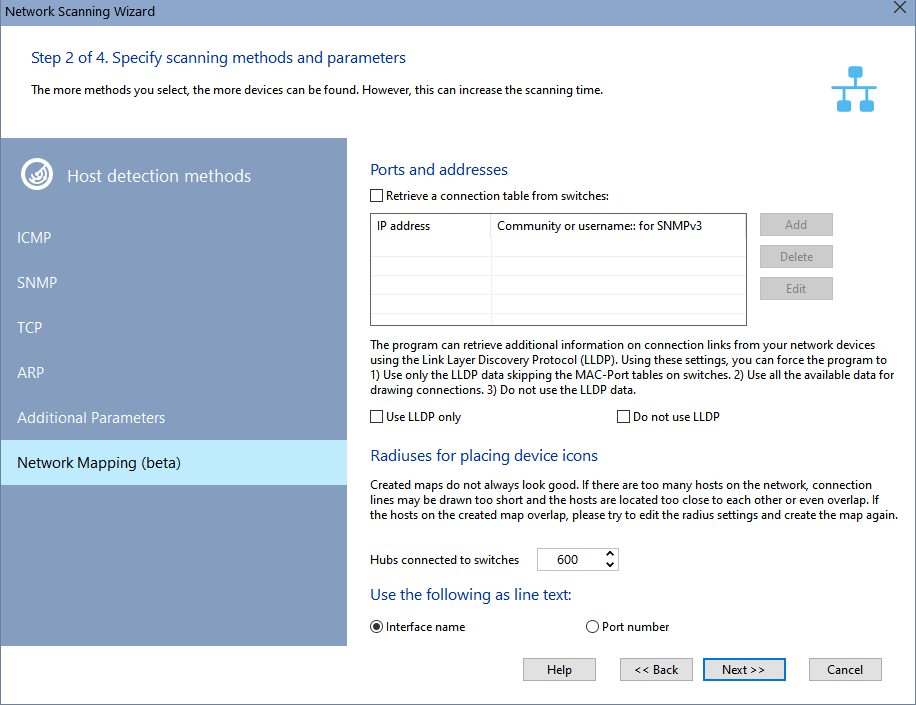
If you know exact IP addresses of managed switches on the network and their communities (Community strings), you can specify them in the switch list before starting the scan and enable the Retrieve connection table from switches option. This gives more assurance that links between devices will be drawn. If this parameter is not enabled, the program will try to obtain the link information only from managed switches found during the IP address range scan.
The program can receive the additional data for drawing links using the Link Layer Discovery Protocol (LLDP). This mechanism allows you to build links between managed switches. With these options you can:
- Use only this data, not taking into account the information of the MAC-Port tables.
- Use all the data (SNMP+LLDP).
- Do not use the LLDP data.
Device Icon Alignment Radiuses
Created maps do not always look good. If there are too many devices on the network, connection lines may be drawn too short and the devices are located too close to each other or even overlap. If the devices on the created diagram overlap, please try to change the radiuses and create the network map again.
If devices overlap on the network map, increase the radiuses. See the picture below. It contains the radiuses that can be configured:
 Hubs connected to switches
Hubs connected to switches Devices connected to switches
Devices connected to switches Devices connected to hubs
Devices connected to hubs Local printers
Local printers
Line Captions
You can specify what to use as line captions when creating the network map: the interface name (for example, FastEthernet0/11) or just the port number (for example, :11).
After setting all the parameters, the Scanning Wizard proceeds directly to the network scanning. Click the Next >> button to proceed.
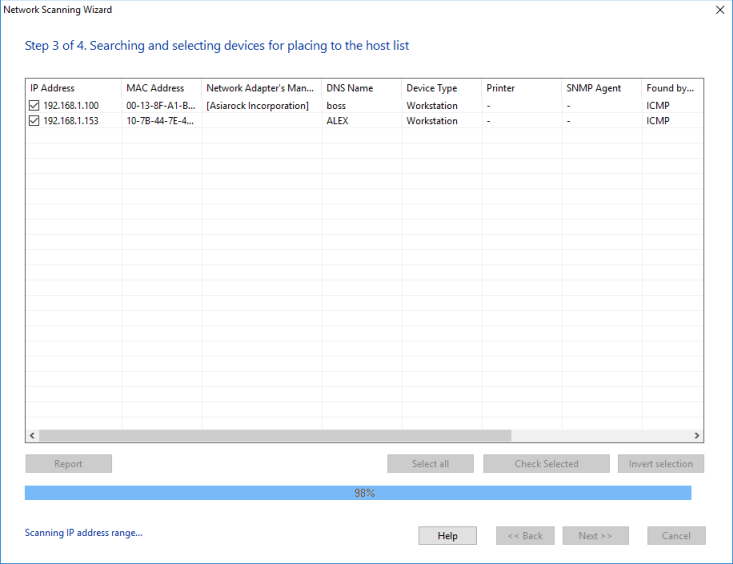
![]() 5. Step 3. Finding and selecting computers for placing on the monitoring list.
5. Step 3. Finding and selecting computers for placing on the monitoring list.
The scanning process starts immediately. First, the application attempts to detect networked and local printers. This procedure may take long time. During the process, the application may fail to respond to requests, and the Stop button will be unavailable. Next, the scanner will search for devices through NetBIOS, what also may take some time. After the completion of the two preparation procedures, the application starts the actual search through all IP addresses within the ranges originally defined. The progress of the process will be indicated by the progress indicator and the "Scanning IP range..." status in the bottom-left corner of the Wizard.
The process can be stopped by clicking on the Stop button.
Hosts found during the scanning will be added to the results list. There is a way to change the type of the device found from the results window. For that purpose, select the required record (multiple selection is allowed) and then open the context menu. On that menu, select the device type to be set.
You can have the program add only selected hosts to the monitoring list by ticking those hosts on the list. The buttons Select All, Selected, and Invert Selection will help you with the selection of multiple hosts.
Click the Report button to export all scanned information (with the scanning settings and parameters) to a CSV file. This report can help the developers of the program to give you a hand if you stumble over any problems when forming the list of network hosts.
When the scanning process is over, move on to the final step by clicking on the Next >> button.
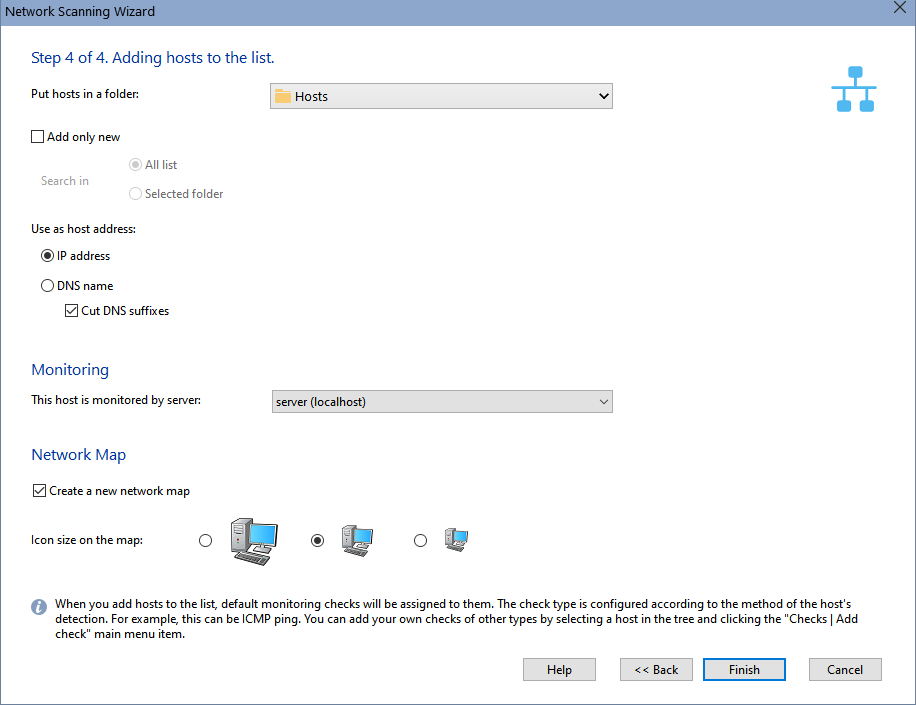
![]() 6. Step 4. Placing hosts on the monitoring list.
6. Step 4. Placing hosts on the monitoring list.
On this step, the wizard will prompt you to select a current node on the monitoring list, where it would place the hosts it has found. Before placing found hosts on the list, you can set additional parameters:
- You can specify, what the wizard is to Use as a host address: the host's IP address or its DNS name. For networks with the dynamic IP address allocation, select the DNS name option, for this attribute in this case will remain constant. For networks with static IP addresses you can select using the host's IP address as the name.
- Cut DNS suffixes. The wizard attempts to use hosts' specific DNS names as captions for the nodes. Such names often have the so-called suffix; e.g., mary.dep1.orgname.com . When this option is selected, the caption by the node will appear as mary.
- If you want to add only new hosts that are not in the monitoring database, use the Add only new option and specify where to look for existing hosts.
- For the Pro version, specify the monitoring server that will poll the added hosts.
- For the Pro version, choose whether you want to create a new network map or simply add hosts to the list. Specify the device icon size for the new network map.
Once you have clicked Finish, the hosts you have found will be placed to the selected node. The application automatically assigns TCP, ICMP or ARP checks to them.