Share, File, Folder, Directory Access Monitoring and Alerting
The program's main function is monitoring of current user connections to shares. The program allows you to configure alerts and receive notifications when a specified user connects to your folders and opens files. Every new user connection to a share or file access is checked whether it should raise an alert with the specified parameters or not.
Supported Events for Auditing, Logging, and Alerting
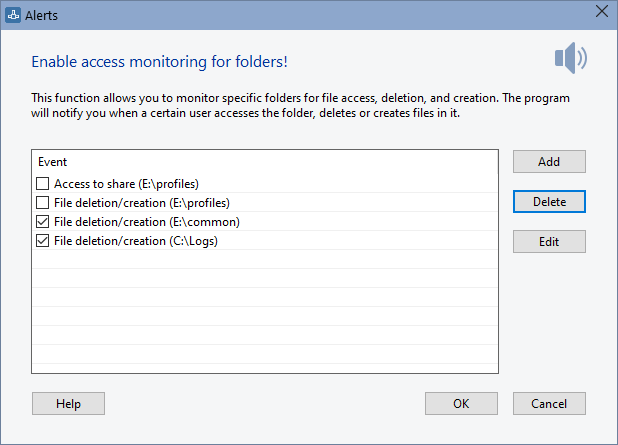
The program supports the following types of events which can be monitored, recorded to the alert log, and alerted via email, sound, and other notification methods when remote users access your shared folders and files:
- User Connection
A user with specified username or a user from computer with specified DNS, IP, or MAC address connects to your shares. - Access to Share
A remote user accesses the specified shared folder or file. - File Deletion/Creation
A user creates, deletes, or renames a file in a specified folder (without detecting the username or the remote computer name). - Opened Files Count
A remote user opens a large number of files (when the opened file count exceeds the specified limit). The program can also monitor the total file size of files opened by a user.
Please read the use cases below. We highly recommend you to read them in order to understand what the program can do for the file and folder access audit purposes in your company.
Notification Types
- Showing a screen message
- Sending an e-mail message
- Running an external application with the necessary parameters
- Playing a sound
- Writing to the log file
- Disconnecting and adding the user to the black list
Use Cases
1. For example, you expect your co-worker to write an important file to your share. In this case, you need to configure the "User connection" alert and specify his username in the alert settings. After doing this, the program will monitor all incoming connections waiting for your co-worker's connection. When the desired connection is established, the program will notify you.
2. A server has a share with important files and folders and you would like to audit remote users' access to that share. Create the "Access to share" alert, specify that important folder, and all users accessing the folder will be logged.
3. A server has a share with important files and folders and you would like to know what files and folders were deleted, created, or renamed. Create the "File deletion/creation" alert, specify that important directory, and all file modifications will be logged. If you want to detect who deleted or created a file in a share, you will need to enable the share access audit in the system. Learn more about this...
4. A server has a share with important project files your team working with. The normal working process is when your team members work with some part of the files, only with necessary ones. You would not like some user to copy or scan the entire project folder. You can configure the "Opened files count" alert in this case. The number of opened files is counter on the per hour basis. You will have to detect an average number of opened files per hour and configure the count limit somewhat higher than the average count to avoid false alerts. When someone decides to copy all the folder, the program will notify you or an administrator about that and you will be able to warn that employee.
You can also configure the total opened file size limit instead of the opened file count limit. When a user reads a file, the program will add the file size to that user's personal count and compare it with the configured limit (per hour).
Please note, that the program cannot distinct whether that user downloaded the whole file or only its part. So the counts should not be considered as 100% true information. The program summarizes full file sizes so the total opened file size count will be always larger than the number of bytes downloaded by that user.
The system can generate excess file openings. For example, when a user browses folders using Explorer, it can read some files to generate preview images for them.
Related topics on working with connection alerts and notifications:
Inventory Hardware and Software on Network Computers
Monitor Network Servers, Services, Managed Switches, etc.
Monitor and Manage Network Hosts on a Visual Map, Create Network Maps
Monitor Network Bandwidth and the Internet Traffic Usage
Create Network Diagrams, Discover Network Topology
Search Files on Network Shares and FTP Servers
Audit Remote User Access to Shares (Folders and Files)
Free Program for Scanning Networks, Hosts, and TCP Ports